For the second time this week, I wasted some time fixing an infected Windows PC. The intriguing aspect of this infection though is that it was not really a virus – unless you count crude scripts designed to scare and inconvenience the user.
The problem started when an elderly friend was called, so she thought, by Microsoft. It was not Microsoft at all, but a fraudster from, it appears, India. He explained that there was a problem with her PC and offered to fix it. I am not sure of all the details, but she ended up paying £20 (after negotiating down from a higher figure) to a bank account in Calcutta.
While this does not sound like something any sane person would do, no doubt these people are suitably convincing after years of practice. It is also true that Microsoft has support staff in India though note that the real company NEVER rings out of the blue with a virus warning so if this happens to you, it is a scam.
I found some payment forms on her PC. They include all the right logos.
The criminal got her to install TeamViewer and I found an entertaining batch file which perhaps he ran to simulate a security product. Here is part of it:
echo license key received
start /w wscript.exe C:sleep2000.vbs
echo:
echo:
echo:
echo Windows License is activated for Lifetime.
start /w wscript.exe C:sleep2000.vbs
and concludes:
echo Your license key has been succesfully activated in your computer..
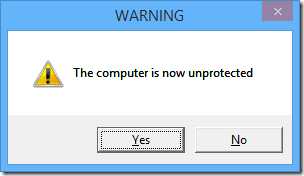
echo Now computer is protected from hackers.
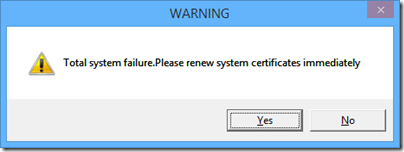
She thought that was the end of it, until she restarted her PC. First, she was prompted to run an executable called AA_v3.exe. If she cancelled, she got a message:
You have been hit by a stuxnet virus, you may lose all your files and folders
and then:
and
This is a simple .VBS script that displays message boxes in a loop.
Next, the computer shuts down. Why? Because the “stuxnet” message was a command in her startup folder that looks like this:
%windir%\system32\shutdown.exe -s -t 120 -c "You have been hit by a stuxnet virus, you may lose all your files and folders"
This runs before the other messages so you end up with a scary command prompt, more scary messages, and then your PC shuts down.
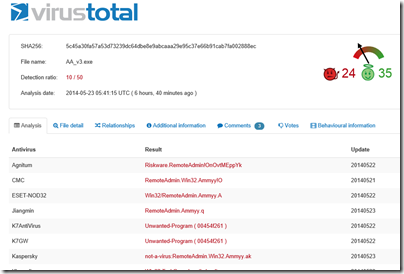
I am not sure what happens if you DO run AA_v3.exe. This, it turns out, is free remote control software called Ammyy Admin. This is so often used by scammers that there is a warning about it on the vendor’s web site:
!!! If you receive a phone call claiming to be from ‘Microsoft’ or someone claiming to work on their behalf, telling you that you have a virus on your computer or some errors which they will help you to fix via Ammyy Admin, it is definitely a scam.
Of course victims will not see this warning.
If you run it though, maybe the criminal can connect and cancel the shutdown before two minutes is up, and use the PC in a botnet. Or maybe there is a follow-up call demanding more money to fix the problem. Who knows?
The attraction of these low-tech scripts (for the fraudsters) is that anti-virus software will not detect anything amiss – though in fact, Ammyy Admin is so widely used for criminal purposes that 10 out of 50 anti-virus products used by Virustotal do report it as a “risky” executable.
The fix in this case was to log on using a different user profile – Safe mode would also have worked but I was working remotely. Once logged on I was able to remove the startup entries and run some other malware checking tools; ideally you would reinstall Windows but this is inconvenient for a home user.
The problem as ever is that if you know criminals have had use of a machine, you do not know what else they may have done.
This scam still seems to be common and profitable for the fraudsters, and will continue I imagine, unless both source and target countries make a real effort to find and prosecute those responsible.