It’s a typical scene of carnage. That nice Pentium IV box which the family got for Christmas takes ages to start up now, and when it does finally kick into life there are a multitude of flashing icons down there on the right. Browsing the web is kinda strange, with popovers, popunders and search windows everywhere you look. There’s Norton Antivirus, ZoneAlarm, Adaware, Spybot and some other fancy utility running in the background, installed because they had a few virus problems and friends reckoned that lot would sort them out. Oddly enough they still get viruses; maybe the Norton update thingie isn’t working quite right, or else the subscription expired, or else the virus emailed itself to a few million machines on the Internet before the AV guys got their signatures updated. So nothing quite works; but fortunately some nice people out there have just emailed a patch that will fix everything. Just double-click the attachment…
What a nightmare. Of course its Microsoft’s fault, Windows is so full of bugs isn’t it? Not like those nice Apples, or the strange Linux thing the neighbour’s son is running. Looks like Microsoft is losing another customer. But hey, let’s backtrack a year or two. July 26 1993; Windows NT, or New Technology, is released to manufacturing. A brand new operating system masterminded by ex-Digital guru Dave Cutler, NT was designed to be portable, reliable and secure, in contrast to the precarious tower of bricks that was DOS and Windows. As a server, it was designed to have the resilience and capability of Unix but with an easy-to-use Windows graphical interface in place of the arcane Unix command-line. Windows NT 3.1 was a relative failure in the market, but it was a solid piece of work. Now, over a decade down the line, both the consumer and server versions of Windows are based on the work that went into Windows NT. So why on earth are so many PCs out there in such an appalling state?
The answer is that Windows has been vandalized. Contrary to rumour, Windows XP and in fact all the NT-based series are fundamentally both reliable and secure. Secure? I can almost hear the chuckles. It’s true though. There’s a fine-grained security system in place which means that every process and every user can be restricted in what it can do. The NTFS file system is a secure file system. Every directory and every file supports 12 different permissions assigned per-user or per-group. Windows also has a carefully designed structure of file locations. System files in the Windows directory; applications in Program Files; application settings and user files in Documents and Settings. The registry, a central configuration database, is also carefully structured, with user settings separated from application and system settings and everything restricted by security settings. The idea is that only system administrators need access to system-critical files. Users only need read-write permissions for their own directories and their own part of the registry. That way, everything stays in order, right?
Unfortunately the world did not play ball. You see, back in the days of Windows 3.1 and earlier, and on the Windows 95 series, the user reigned god-like over her machine. Remember that little log-on dialog that came up in Windows 95, boldly asking for a username and password? And if you breezily dismissed it with Cancel, Windows went ahead and opened anyway? OK, you might not be on the network, but that’s another thing. You could always get at anything on your own PC. The application vendors took advantage of that. Their installers cheerfully ignored Windows guidelines, installed files into the Windows directory, put user data into Program Files, wrote all over the registry, created directories right outside the official structure, and so on. Users didn’t mind too much, because all they care about is that stuff works, which it mostly did.
So now along comes Windows NT, 2000, and XP. There are all these applications still ignoring the guidelines, and users installing them on this new series of Windows editions. Everyone wants an easy life – the users, the application vendors, even Microsoft. When users logged on without the permissions of a system administrator, stuff stopped working, the users complained, and the support guys fixed it by giving them administrator permissions. Since that fixed it, the application vendors had no incentive to change the behaviour of their apps. Even some Microsoft consumer applications made that assumption. The result being that huge numbers of Windows users log on as administrators. Who’s to blame? Not really the designers of Windows; the design is OK. Arguably the application vendors, but they simply went along with the crowd. No, the primary culprit has to be Microsoft, not for bad design, but for not pushing this issue hard enough.
A Linux desktop called KDE comes up covered in bombs if you log on as root, the equivalent to system administrator. Microsoft should have done that with all the NT-based series. With XP Home, aimed at non-expert users, there should be big warnings everywhere if you log on with admin rights. I’ve just taken a look at the dialogs you get when setting up a user. There are two options, Computer administrator or Limited. As you’ll see from the illustrations below, the choice is a no-brainer. With the Administrator type you can do what you want, everything works. With the Limited type you need help installing stuff, and a mysterious subset of programs might not work. The word – ahem – “security” is nowhere to be seen.
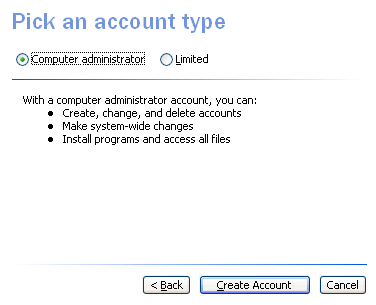
Exhibit A: What you get with a "Computer administrator" in XP Home.
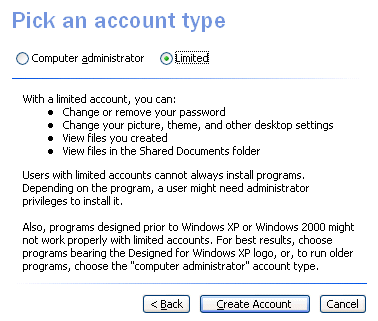
Exhibit B: What you get with a "limited user" in XP Home.
With these dialogs, Microsoft is virtually insisting that you create system administrators. At the same time, those who worked so hard to design proper security into Windows must be in tears.
What would have happened if the user dialog, instead, had “Normal user” as the default, and “System configuration user” as the other. And if you selected “System configuration user”, it would have a huge red exclamation mark explaining that this type of user should not log on when the system is connected the Internet, and should not run applications other than installers and configuration utilities. Of course everyone would be a “Normal” user, their apps would break, and they would howl. But the storm would pass, because vendors would fix their apps. And it would be harder for worms and viruses to flourish, because they typically only execute with the permissions of the user. As it is … well, you know the story.
Here's another amazing thing. Let's say you've done the right thing, you set up and use "limited users". Unfortunately some app needs fixing up. You need to adjust the permissions on a particular file or folder, to give a limited user greater access rights. Can you do this in XP Home. Sure ... you just, err, boot into safe mode, right-click the folder, properties, and there's your security info. Safe mode! Not what a typical home user is going to think of first, when an app doesn't run. Oh yes, and you might need to fire up regedit and tweak the security on some entries there as well. Isn't it astonishing that XP Home doesn't provide an easy-to-use wizard for editing limited user rights on a particular directory? Understandably, most home users will do the obvious thing, and revert to administrator permissions for everyone. Party time for malware.
Other factors
There’s no silver bullet. Even if Windows users did not run with admin rights, there would still be problems. I can imagine devious spyware, adware, worms and viruses simply saying. “In order to benefit from our free software or enhanced search or exciting pictures or discount prices or hot stock picks or whatever, enter your admin password now.” And some people would. There’s also the bugs to think about. RPC (Remote Procedure Call) vulnerabilities, cross-site scripting, ActiveX controls that should be safe and are not, buffer overflows and the rest. I don't believe the general quality of Microsoft's coding is any worse than that of other companies; in fact, Microsoft's software is generally of higher than average quality in my experience. But Windows has suffered from some irresponsible defaults in very widely used applications, such as Outlook and Outlook Express, as well as mistakes like installing too much stuff unasked for, even things like web servers and database servers that are big security risks. It’s been a poisonous cocktail of wrong decisions by Microsoft, bugs, the popularity of Windows, and the determination of malware and adware authors to get their hooks into your system. For the most part Microsoft has I think learnt its lessons, though sadly not yet on the user rights front.
The fact remains though that Windows is thoroughly vandalized. And I’m sad about that because I like it. It’s reliable, it’s powerful, it’s relatively easy to use and manage. It works very well for me. It’s tragic that it is now so often weighed down with useless utilities, and spoiled by arguably well-meaning anti-virus software that slows down the system, fails to stop virus outbreaks, delivers a false sense of security, and disables useful features like Windows scripting.
Is the situation better in the corporate world than at home? Yes, it is to some extent. Organizations large enough and lucky enough to have well run IT systems can configure and lock-down Windows sensibly. There are still too many users running with admin rights though. And once you get down to small businesses and home offices, you are right back in the jungle. Unfortunately, the corporate and consumer worlds are all on same network, called the Internet, so what happens at home damages everyone.
Where do we go from here?
I wish I knew. Bearing in mind the horrible state of many systems out there, you can hardly blame users if they try something different. If Windows becomes a minority taste, the problem will have solved itself, though the vandals may (or may not) succeed as well with other targets. I’m convinced of one thing though. Windows XP Service Pack 2, generally a good step forward security-wise, does not go far enough. There’s only one entity that can force the issue on user permissions, and that’s Microsoft. We’ve suffered long enough from the supposedly easy option.
Copyright Tim Anderson 27th July 2004. All rights reserved.
