A couple of days ago I posted about programmatically detecting whether UAC is enabled. I was proposing to read a registry entry. Thanks to the power of blogs, my post drew a comment from Andrei Belogortseff, who has posted C++ code that does this properly. His library has functions for detecting whether the current process is elevated, detecting whether UAC is enabled, and running new processes both elevated and non-elevated (the last of these is the hardest to do).
I liked the libary but wanted to use it from .NET. I compiled his code to a DLL and did a C# wrapper; then I considered the hassles of adding a dependency on the Visual C++ runtime libraries. I therefore did a quick C# implementation of the functions I cared about; I haven’t included the code for running new processes. Please go ahead and download the code, and let me know if you have any suggestions, or even if there is a much easier way to do this that I have missed. There is an app called UACElevationCheck, which calls functions in VistaTools.cs.
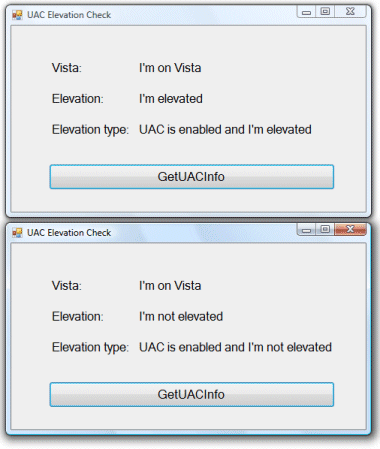
The code is only intended to be called from Vista and will throw an exception otherwise; of course you can modify it as you like.
I’ve included a function IsReallyVista that looks for a Vista-only API call, rather than relying on the reported version information. This is because the version information is unreliable if the app runs in a compatibility mode. On the other hand, IsReallyVista is a hack; if you don’t like it, use IsVista which uses the version information instead.
You may be able to do this using the System.Security namespace rather than PInvoke. I had a quick look but the PInvoke code seemed easier to me, especially since Belogortseff has already done the real work.