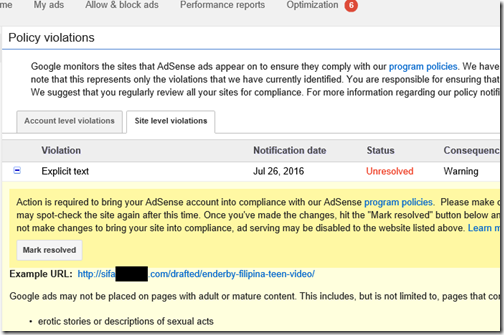
I attend several trade shows during the year, and at one of these Blue was showing off its microphones and headphones. These are the world’s best headphones, said one of the representatives. I expressed some scepticism and she promised to send me a pair to try.

The Mo-Fi, which sells for around £249 or $349, is an unusual set of wired headphones in that it includes its own amplifier, powered by a rechargeable 1020mAh battery. It takes 3-4 hours to charge, which gives you around 12 hours of play, though if the battery runs out it is not fatal as you can also use the headphones in passive mode.
The amplifier can also be used in “On+” mode which boosts the bass slightly. Despite this feature, these headphones are designed for those who like a natural sound rather than one which exaggerates the sonics for instant appeal but later fatigue.
First impressions
When you unpack the Mo-Fi headphones from their solid cuboid box you immediately get an impression of a well-built and high quality product. This is an over the ear design with a metal frame and what I would describe as a modernist, industrial look; opinions on this will vary but personally I am more interested in the sound and the comfort. If you are looking for a svelte and elegant headset though, these will not be for you.

In order to achieve a good fit whatever the size of your head, Blue has put hinges on the earcups so you can tilt them inwards, reducing their distance from the headband. You can also adjust the tension on the headband to get a looser or tighter grip according to taste. I find the comfort OK though not the best; the problem is that the solidity of the design means greater weight (455g) so you notice them a bit more than a lighter and softer set. That said, I can wear them for an hour or two without strain.
Blue supply two cables, a short 1.2 meter cable for iPad and iPhone which includes volume, pause and microphone, and a 3 meter cable for other sources. There is also an adaptor for headphone amplifiers with a 1/4” jack socket, and another for aeroplane seats with the old dual jack sockets. Finally, you get a well made soft case with a carry strap.

There is no mention of Android phones in the short manual, but the iPhone cable works fine for microphone and pause/play. The in-cable volume controls only with Apple devices though, because of annoyingly different hardware standards.
Sound quality
The philosophy behind the Mo-Fi seems to be that most of use compromise our listening experience by using headphones or headsets that do not do justice to the music. In part this is because of inferior headphone amplifiers in many mobile devices, which the Mo-Fi’s built-in amplifier mitigates though cannot fix completely (since it is not bypassed).
I tried the Mo-Fi on a variety of devices, including Android phones, an iPad, and an audiophile headphone amplifier (Graham Slee Solo). I compared them to several other headphones and headsets, using music including classical, jazz, rock and pop. I listened to the Mo-Fi mostly with its amplifier on, but not in the on+ position.
The good news: the sound is excellent. It is clean, precise, extended in frequency response, and generally neutral in tone though with slightly recessed high frequencies.
What is the effect of the built-in amplifier? It depends. Using the external headphone amplifier, the built-in amplifier does little more than increase the volume. You can get the same result by turning up the volume in passive mode. On a phone though, the effect is more marked, and you can hear improvement in quality as well as volume. That is what you would expect.
However, while the Mo-Fi sounds good with a phone, I was surprised how much much the sound improved when using the Graham Slee amplifier. Since a Solo costs more than the Mo-Fi, perhaps that is not surprising, but it does illustrate that unfortunately there are still compromises when using a smartphone for music.
What kind of sound do you get from the Mo-FI? Since it is neutral and clean, the Mo-Fi sounds good with all kinds of music, though they are not bright, to the extent that you should avoid them if you like a bright sound. The bass I found particularly tuneful, for example on My Funny Valentine by Miles Davis, which is a rare quality. Listening to the magical Four Seasons by the Academy of St Martin in the Fields I found the Mo-Fi smooth and engaging but not quite as clear or sweet as on high-end Sennheiser headphones.
Playing By Your Side by Sade, which has deep bass that is difficult to reproduce, the Mo-Fi coped well with all the bass energy, though losing the cymbals on this track sounded slightly muted.
Death of a Bachelor by Panic! at the Disco is always an interesting track to play, thanks to its ridiculous bass extension. The Sennheiser HD 600 (about the same price as the Mo-Fi though an open back design) sounds too polite on this track, failing to reproduce the bass thunder, but in compensation sounds tuneful and clean. The Mo-Fi makes more effort to reproduce the bass but on this very demanding track it does tend to blur (a rare failing with these cans) making the tune harder to follow.
On a modern recording of Beethoven’s 5th Symphony (San Francisco Symphony Orchestra conducted by Michael Tilson Thomas), the Mo-Fi does a fine job reproducing the scale and drama of the opening movement, no trace of blurring here. It is a big sound though again slightly let down by the treble.
No, these are not the best headphones in the world, but they do deliver outstanding quality at what, in audiophile terms, is a moderate cost.
If your preferences veer towards realistic bass and a big, articulate sound you will like the Mo-Fi. If you prefer a sweet, detailed treble with lots of air and space, these might not be for you.
There is one annoyance. One is that the amplifier switch is slightly crackly on my Mo-Fi. I worry that it might get worse over time.
Blue quotes a “15Hz-20kHz” frequency response for both the amplifier and the drivers, but without any indication of how much frequency drops off at the extremes so these figures are meaningless. Impedance is 42 ohms.
Summary
The sound quality is great, but the downside is that the Mo-Fi is relatively heavy and bulky and so some that will be a considerable disadvantage, especially as it does affect the wearing comfort. I can wear the HD 600 all day, whereas after a couple of hours I wanted to remove the Mo-Fi (it might become more comfortable as it wears). The closed back design means you get good sound isolation, which is good or bad depending on how much you want to be able to hear external sounds while listening to music.
If that doesn’t put you off, the Mo-Fi is well worth a listen. It’s well made, thoughtfully packaged, and sounds better than most of its competition.