This was my second marathon. The first was in October last year and went super well; I targeted 3:45, used the Pfitzinger/Douglas (Pfitz) 18/55 schedule (in the book Advanced Marathoning) for training, and while it was fatiguing I finished in 3:37 and (as I now know) in relatively good shape.
This time around I wanted to beat 3:30 and repeated Pfitz 18/55 but with faster pace. Training went well overall, no major injuries, and I mostly hit the workout paces though I find what he calls the V̇O2 Max sessions difficult to achieve; these are the most demanding sessions intended to improve one’s maximum rate of oxygen consumption during running.
Before the race

Got to Manchester Saturday afternoon, didn’t get to run at all though Pfitz schedules a 4 mile recovery run saying it is mainly there to keep you from fretting. Difficult to carb load when travelling but I did my best with a big bowl of cereal for breakfast followed by a bacon roll later, packed lunch with chunky cheese sandwiches and fresh fruit, then I consumed a mid-afternoon Ploughmans with a fruit smoothie and in the evening, a delicious goats cheese flatbread. I also drank loads of water, not sure exactly how much but several pints during the day. I think this did help as I was well hydrated before the race.
Set the alarm for 5:30am not that I needed to; didn’t sleep brilliantly. Cup of tea and sourdough roll early (Pfitz suggests eating 3-4 hours before running), more water. Then I headed for the start on the first tram from my hotel at about 6:25; no reason to be so early except that I didn’t have anything else to do! Always enjoy chatting with other runners and their supporters.
My first marathon had fewer than 1000 runners, this one claimed 36,000 though I am sure the actual number was a bit less. All a bit different though. Arrived Old Trafford tram stop, 10 minute walk to the start area. Dropped my bag at around 8:00am and was a little cold in my club vest, did some half-hearted short warm-up runs and took advantage of the portaloos. This was a success actually, the benefit of the early start meant that I had plenty of time to get ready as it were and had zero GI issues during the race.
I was in bronze wave which was the fifth to start after Elite, White, Red and Blue. Each wave had I gather up to 1800 runners which is biggish and I found myself towards the back of the wave for some reason. This didn’t matter as such, but the 3:30 pacers were towards the front and it wasn’t possible therefore to start with them. More on this later.
The Race
Off we go and I am trying to go no faster then a 7:45 pace (all my figures are in miles) and no slower than 8:00. Some congestion but it went fairly well and the miles started ticking by. Took an energy gel at the start and another 4 miles in. Skipped the first water station, grabbed a bottle at the second, but found drinking quite hard while running, I have learned that I can’t take a big gulp as it can easily turn into a coughing fit. Did my best; at least with the bottles you can carry them for a bit and take occasional sips.
After maybe 6 miles (can’t remember exactly), I catch up with a 3:30 pacer (there were two) and had a chat. Now, I knew from my Garmin that I was on target for sub-3:30 but of course having started at the back of the wave the pacers were a little in front. It was tricky though; the guy said he was currently running ahead of pace because he had a bathroom break and was now catching up with the other pacer. So I didn’t want to keep pace with him as it would be too fast. Off he went into the distance.
At the half-way point I finally caught up with the other 3:30 pacer. This was odd because he was now quite a way behind first guy. I asked about this and he said his fellow pacer was more than a minute ahead of time. He also said he was a bit ahead, and his plan was to to slow down at 26 miles and then wave people past to get their time. I concluded that my best strategy was to try and stay ahead of him.
I was more fatigued at this point than I was when half-way in October but there were two good reasons for that. One was that my pace was about 7:54/mile versus 8:16 or so in October. The other was the heat; we were running in up to 20 degrees Celsius and bright sunshine whereas October was overcast with occasional light rain and much cooler (I don’t know the exact temperature).
Another thought: for this event I trained in the cool of the winter and then ran in relatively warm conditions; where last time I trained in the heat of the summer and then ran in relatively cool conditions – an easier transition!
Anyway I was keen to get to 20 miles as Pfitz calls 13-20 the “no-mans land of the marathon” when you can easily lose pace. Kept the pace fairly well and was helped by the pacer because if he appeared beside me I knew I had to run faster!
Got to 20 miles and by this time I was seriously fatigued. I took my first carb-packed SIS beta fuel at this point and told myself it would help me to keep going.
The last 6 miles were tough. I can’t say I hit the wall; I lost a little pace but it wasn’t terrible – my slowest mile according to Garmin was mile 24 at 8:04 pace. Heat was getting to me, really needed water at the last drink station. It was difficult to drink enough, but poured the rest over my head, great idea and I should have done this before.
It is hard to describe the mental battle that was taking place in those last miles. I told myself to just keep running even though I no longer had the energy for it. I told myself to run fast so that the ordeal would be over quicker. I thought of my family and friends tracking me and did not want to disappoint them. And again, if the 3:30 pacer appeared, I did my best to run faster (and in the end, I did finish ahead of him, but a few seconds behind the other 3:30 pacer).
The crowd at Manchester was fantastic and it was great to hear all the shouts of encouragement including my name from time to time (name were shown on the bibs). I also passed plenty of runners walking and told myself that I would not do that. Just one parkrun to go. Just two miles to go. Then there is a sign that says “welcome to the finish straight,” great news but I did not have it in me to up the pace. Kept running, tried to smile for the camera, crossed the line, and then there was a weird moment: is it really OK to slow down now?
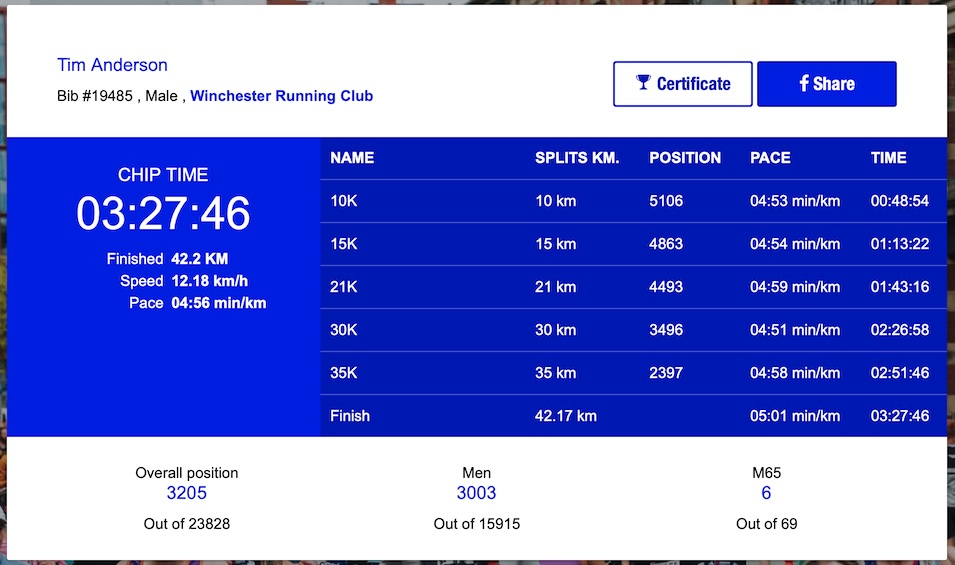
I was pretty sure that I had beaten 3:30 but did not get the exact time until later (not carrying a phone). 3:27:46, a personal best by over 9 minutes and a good for age for London next year I hope, with over 24 minutes below the required time (V65 M).
After the ordeal
Finishing a marathon can be anti-climactic. I felt good about my time but also very fatigued, and the first thing you do after finishing at a big event like this is quite a lot of walking, since the organisers have to keep the finish area clear. So picked up a bottle of water (good thinking!), walked to medal area, picked up tasty non-alcoholic tin of beer (chilled! Nice), walked to picked up bag, quite a long way with several lorries for each start wave, then walked to T-shirt area, then you come out of the finish area and eventually to a sign that says Piccadilly Station 14 mins walk, my hotel was near there so I just plodded on, eventually sitting down to a lovely latish lunch there with a cold beer and some fellow finishers.
I can’t really fault the organization, the start was smooth and on time, the facilities were good, the medal is nice, all very professional, but there is inevitably a lot of standing around at the start and walking at the end.
The pacers worked hard but were not ideal for me. I would prefer that they ran closer together and with even splits, though they did finish pretty much on the button.
While I was happy with my time it was actually slower than the 3:19 VDOT predicted from my best half in February; I think this shows the impact of the heat as my effort was as great or greater.
Despite piling on the suncream I caught the sun in a few spots, my advice if you are running this summer is don’t forget the back of your legs and all round your arms as that is where I went wrong. Wore a cap which I do think helped.
Finally, kudos to the Pfitz plan and book which got me through again without any calamities, such a great resource.