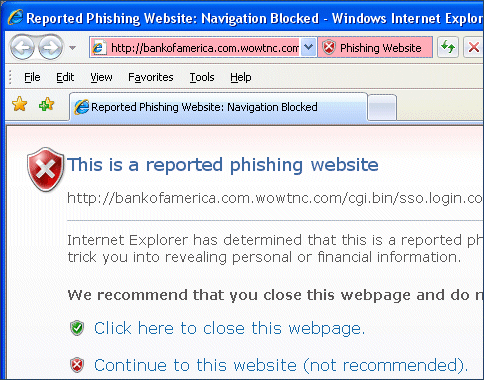
I remain concerned about application compatibility and Vista’s virtualization. Here’s an example. After setting up a Tablet PC with Vista RC2, I installed one of my favourite time-wasters, a game called Jack Bridge; not a major piece of software, but typical of countless existing Windows applications that users will want to install on Vista. Setup seemed to go OK, though Vista threw up this perplexing and alarming dialog:
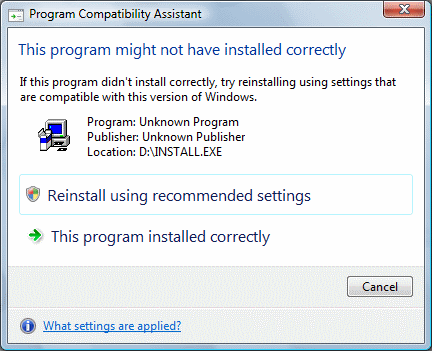
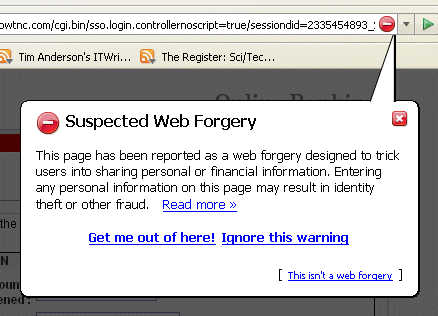
Trouble is, at this stage I did not know if the installation was successful or not. Nor is it obvious what the consequences of the two options might be, or what Cancel will do. I took the view that I would rather try it as-is for the moment, and clicked “This program installed correctly.” And so it seemed, to begin with. Everything was fine until I used an option in Jack to check for updates from the Web. The update downloaded, but failed to install with this error:
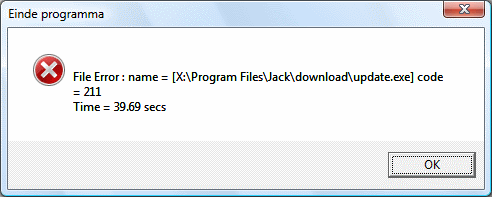
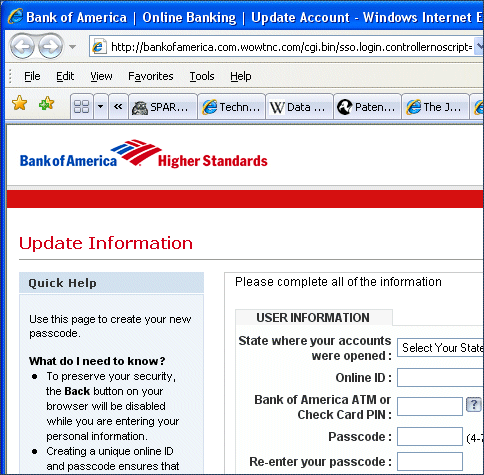
To be honest, I was expecting something like this. The application was attempting to download the update to its folder in Program Files, and then to execute it. Neither operation could succeed, since UAC makes Program Files read-only. I can’t explain the Dutch; it looks like the app has imperfect localization. As a further test, I tried logging on as a different user and running Jack. This was really bad. Jack failed to run, warned me of severe errors, and advised that I contact my reseller. The problem here is the virtual store. Vista tries to help applications such as Jack by seeming to allow read-write access to Program Files, but in reality writes the data to a user-specific virtual store. This means each user gets a different view of what should be the same files. It all happens behind the scenes; if it goes wrong the user has no idea what has happened. I mostly approve of UAC, but I fear the virtual store may cause more problems than it solves.
In the case of Jack, I found a good workaround. I uninstalled it, then reinstalled to a location in my user directory. Jack has read-write access without trickery, and everything works, provided I always run as that user. How many other applications out there are going to have problems with UAC? My guess is a lot. Some of the above may improve in the final release – maybe the dialogs will be better worded – but I’m not expecting fundamental changes. Existing applications are going to cause users immense compatibility hassle. In consequence, they may disable UAC, which will greatly reduce Vista’s security; or they may decide Vista itself is more trouble than it is worth.
Let me be clear: disabling UAC is not a good idea. Users running with local admin rights is a large factor in the Windows security problem, and UAC is a reasonable solution. But I’m expecting the worst. When Vista hits the world at large, will the buzz will be: turn off UAC or nothing will work properly?
Update
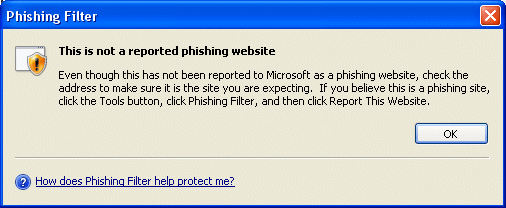
I couldn’t help wondering what would have happened if I had let Vista “Reinstall using recommended settings”. I had a struggle fulling uninstalling Jack in order to try this option. Eventually I found the registry key at HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted, and deleted the reference to install.exe. Reinstalled, and when the dialog appeared chose “Reinstall using recommended settings.” The installation tried to run again, but immediately closed; I guess because the installer considered the application already installed. I removed it through Control Panel and once again reinstalled – my hunch is that the “recommended settings” were automatically applied. If I show properties for the application shortcut, it says “Run this program in compatibility mode for Windows XP (Service Pack 2)”. However it doesn’t seem to help with the specific problems I encounted. Online update still failed, and when I logged on as a different user and tried to run Jack, I got the “please contact your reseller” dialog.
I am not trying to be difficult here. Rather, I’m trying to replicate some typical scenarios when users are confronted with these difficult dialogs.
Technorati tags:
vista,
uac,
windows