A puzzled Outlook 2007 user asked me why his Outlook 2007 archive folders were empty. Investigation led me to this dialog, found at Tools – Options – Other – AutoArchive:
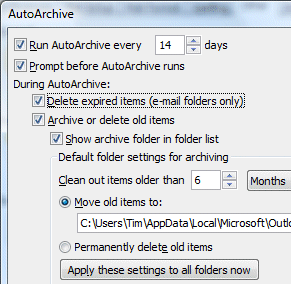
This is actually from my own Outlook; but as you can see, it is set to move old items to an archive folder. Note that the option to Move rather than delete is set by default.
However, I was puzzled by the option to Delete expired items (e-mail folders only). What does this mean? In particular, why does it refer to expired items when the rest of the dialog refers to old items? The word expired suggests some kind of non-validity, like an expired subscription, or password, or credit card.
Pressing F1 did not yield anything helpful; but this article explains:
Delete expired items (e-mail folders only) This option is not selected by default. You can choose to have e-mail messages deleted when their aging period has expired. The default period for your Draft and Inbox items is six months, and three months for your Sent Items, but you can change these periods using the Clean out items older than option.
As I understand it, this means that items are deleted after as little as three months if the option is checked; and expired means exactly the same as old. But that’s OK; it isn’t checked by default.
Or is it? For sure, I have never checked that option, nor did my contact, but it is checked on all my Outlook installations, and on his. Take a look: is your Outlook set up like this? I’d be interested to know.
The consequence is that old emails simply disappear. The only dialog the user will see is that auto-archive wants to run. By the way, most people would not imagine that an archive process will delete items. Archive means long-term storage. Words like prune or purge imply deletion, but not archive.
Now, I happen to think that archiving in Outlook is a mess anyway. If you have several machines on the go (which is one of the reasons for using Exchange and Outlook), then you usually end up with several archives, buried deep in hidden folders where nobody is likely to find them without help. It is easy to miss these archive files when migrating to a new machine.
Still, I hadn’t realised that Outlook actually deletes old emails without asking – that is, if I am right and this is (incorrectly) the default.
It may seem a small matter; but there are times when finding that old email, sent or received, is critically important. It is another reason why I am fed up with Outlook 2007: its amusingly obscure dialogs, its broken RSS support, and its disgracefully slow performance.
Update: Duncan Smart below suggests that the “Expired items” refers to emails that have an expiry date set in message options. I must say that makes more sense to me. On the other hand, it isn’t what the help document says, and it doesn’t explain why why my contact had no messages in his archive folder, until I changed the setting. I’ll try some experiments … [slightly later] … if I archive a folder with File – Archive, it does not delete old messages (good); on the other hand this dialog is different because you specify the archive date so it is not a perfect test.
I suspect it is not as bad as I first thought, that the help document is incorrect, and that some other factor must have messed up my contact’s archiving. I hope that is the case.
See also this official help document:
Choosing an option to have items deleted permanently deletes the items automatically when they expire. They are not archived. For instance, if you click Delete expired items (e-mail folders only), this option deletes all messages in all your e-mail folders, such as Inbox, Sent, or Drafts, when they reach the end of their aging periods. The messages are not archived.
So … either Outlook really is deleting messages without asking; or I’m not the only one confused.