Ars Technica published a piece today about insecure network cameras which reminded me of my intention to post about my own experience.
I wanted to experiment with IP cameras and Synology’s Surveillance Station so I bought a cheap one from Amazon to see if I could get it to work. The brand is Knewmart.
Most people buying this do not use it with a Synology. The idea is that you connect it to your home network (most will use wifi), install an app on your smartphone, and enjoy the ability to check on how well your child is sleeping, for example, without the trouble of going up to her room. It also works when you are out and about. Users are happy:
So far, so good for this cheap solution for a baby monitor. It was easy to set up, works with various apps (we generally use onvif for android) and means that both my wife and I can monitor our babies while they’re sleeping on our phones. Power lead could be longer but so far very impressed with everything. The quality of both the nightvision and the normal mode is excellent and clear. The audio isn’t great, especially from user to camera, but that’s not what we bought it for so can’t complain. I spent quite a long time looking for an IP cam as a baby monitor, and am glad we chose this route. I’d highly recommend.
My needs are a bit different especially as it did not work out of the box with Surveillance Station and I had to poke around a bit. FIrst I discovered that the Chinese-made camera was apparently identical to a model from a slightly better known manufacturer called Wanscam, which enabled me to find a bit more documentation, but not much. I also played around with a handy utility called Onvif Device Manager (ONVIF being an XML standard for communicating with IP cameras), and used the device’s browser-based management utility.
This gave me access to various settings and the good news is that I did get the camera working to some extent with Surveillance Station. However I also discovered a number of security issues, starting of course with the use of default passwords (I forget what the admin password was but it was something like ‘password’).
The vendor wants to make it easy for users to view the camera’s video over the internet, for which it uses port forwarding. If you have UPnP enabled on your router, it will set this up automatically. This is on by default. In addition, something strange. There is a setting for UPnP but you will not find it in the browser-based management, not even under Network Settings:
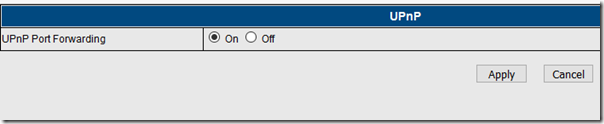
Yet, if you happen to navigate to [camera ip no]/web/upnp.html there it is:
Why is this setting hidden, even from those users dedicated enough to use the browser settings, which are not even mentioned in the skimpy leaflet that comes with the camera? I don’t like UPnP and I do not recommend port forwarding to a device like this which will never be patched and whose firmware has a thrown-together look. But it may be because even disabling UPnP port forwarding will not secure the device. Following a tip from another user (of a similar camera), I checked the activity of the device in my router logs. It makes regular outbound connections to a variety of servers, with the one I checked being in Beijing. See here for a piece on this, with regard to Foscam cameras (also similar to mine).
I am not suggesting that there is anything sinister in this, and it is probably all about registering the device on a server in order to make the app work through a peer-to-peer network over the internet. But it is impolite to make these connections without informing the user and with no way that I have found to disable them.
Worse still, this peer-to-peer network is not secure. I found this analysis which goes into detail and note this remark:
an attacker can reach a camera only by knowing a serial number. The UDP tunnel between the attacker and the camera is established even if the attacker doesn’t know the credentials. It’s useful to note the tunnel bypasses NAT and firewall, allowing the attacker to reach internal cameras (if they are connected to the Internet) and to bruteforce credentials. Then, the attacker can just try to bruteforce credentials of the camera
I am not sure that this is the exact system used by my camera, but I think it is. I have no intention of installing the P2PIPC Android app which I am meant to use with it.
The result of course is that your “security” camera makes you vulnerable in all sorts of ways, from having strangers peer into your bedroom, to having an intrusion into your home or even business network with unpredictable consequences.
The solution if you want to use these camera reasonably safely is to block all outbound traffic from their IP address and use a different, trusted application to get access to the video feed. As well as, of course, avoiding port forwarding and not using an app like P2PIPC.
There is a coda to this story. I wrote a review on Amazon’s UK site; it wasn’t entirely negative, but included warnings about security and how to use the camera reasonably safely. The way these reviews work on Amazon is that those with the most “helpful votes” float to the top and are seen by more potential purchasers. Over the course of a month or so, my review received half a dozen such votes and was automatically highlighted on the page. Mysteriously, a batch of negative votes suddenly appeared, sinking the review out of sight to all but the most dedicated purchasers. I cannot know the source of these negative votes (now approximately equal to the positives) but observe that Amazon’s system makes it easy for a vendor to make undesirable reviews disappear.
What I find depressing is that despite considerable publicity these cameras remain not only on sale but highly popular, with most purchasers having no idea of the possible harm from installing and using what seems like a cool gadget.
We need, I guess, some kind of kitemark for security along with regulations similar to those for electrical safety. Mothers would not dream of installing an unsafe electrical device next to their sleeping child. Insecure IoT devices are also dangerous, and somehow that needs to be communicated beyond those with technical know-how.