I’m just back from AVG’s press event in New York, where new CEO Gary Kovacs (ex Mozilla) presented the latest product suite from the company.
Security is a huge topic but I confess to being something of a sceptic when it comes to PC security products. Problems include performance impact, unnecessary tinkering with the operating system (replacing the perfectly good Windows Firewall, for example), feature creep into non-security areas (AVG now does a performance tune-up product), and the fact that security software is imperfect. Put bluntly, it doesn’t always work; and ironically there was an example at a small business I work with while I was out there.
This business has AVG on its server and Microsoft Security Essentials on the clients, and somehow one of the clients got infected with a variant of a worm known as My little pronny which infects network shares. It may not be the exact one described in the link as these things mutate. Not too difficult to fix in this instance but a nuisance, and not picked up by the security software.
IT pros know that security software is imperfect, but uses do not; the security vendors are happy to give the impression that their products offer complete protection.
Still, there is no doubt that anti-malware software prevents some infections and helps with fixing others, so I do not mean to suggest that it is no use.
AVG is also a likeable company, not least because it offers free versions of its products that are more than just trialware. The freemium model has worked for AVG, with users impressed by the free stuff and upgrading to a paid-for version, or ordering the commercial version for work after a good experience with the free one.
Another key topic though is how security companies like AVG will survive the declining PC market. Diversification into mobile is part of their answer; but as I put it to several executives this week, Windows is particularly vulnerable thanks to its history and design, whereas operating systems like Android, iOS and Windows RT are designed for the internet and locked down so that software is only installed from curated app stores. Do we still need security software on such devices?
My further observation is that I know lots of people who have experienced Windows malware, but none so far who have complained about a virus on their Android or iOS device.
What then did I learn? Here is a quick summary.
AVG is taking a broad view of security, and Kovacs talked to me more about privacy issues than about malware. Mozilla is a non-profit that fights for the open web, and the continuity for Kovacs now with AVG is that he is working to achieve greater transparency and control for users over how their data is collected and shared.
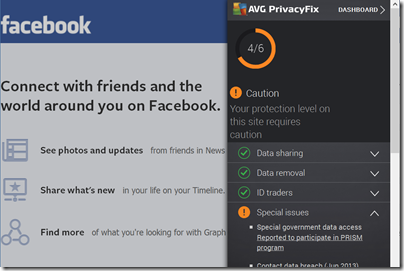
The most striking product we saw is a free browser add-in called PrivacyFix. This has an array of features, including analysis of social media settings, analysis and blocking of ad trackers, and reports on issues with sites you visit ranging from privacy policy analysis to relevant information such as whether the site has suffered a data breach. It even attempts to rate your value to the site with the current settings; information which is not directly useful to you but which does reinforce the point that vendors and advertisers collect our data for a reason.
I can imagine PrivacyFix being unpopular in the ad tracking industry, and upsetting sites like Facebook and Google which gather large amounts of personal data. Facebook gets 4 out of 6 for privacy, and the tool reports issues such as the June 2013 Facebook data breach when you visit the site and activate the tool. Its data is limited though. When I tried it on my own site, it reported “This site has not yet been rated”.
AVG’s other announcements include a secure file shredder and an encrypted virtual drive called Data Safe which looks similar to the open source TrueCrypt but a little more user-friendly, as you would expect from a commercial utility.
AVG PC TuneUp includes features to clean the Windows registry, full uninstall, duplicate file finder, and “Flight mode” to extend battery life by switching off unneeded services as well as wireless networking. While I am in favour of making Windows leaner and more efficient, I am wary of a tool that interferes so much with the operating system. However AVG make bold claims for the efficacy of Flight Mode in extending battery life and perhaps I am unduly hesitant.
On the small business side, I was impressed with CloudCare, which provides remote management tools for AVG resellers to support their customers, apparently at no extra cost.
All of the above is Windows-centric, a market which AVG says is still strong for them. The company points out that even if users are keeping PCs longer, preferring to buy new tablets and smartphones than to upgrade their laptop, those older PCs sill need tools such as AVG’s suite.
Nevertheless, AVG seems to be hedging its bets with a strong focus on mobile, especially Android. We were assured that Android is just as vulnerable to Windows when it comes to malware, and that even Apple’s iOS needs its security supplementing. Even if you do not accept that the malware risk is as great as AVG makes out, if you extend what you mean by security to include privacy then there is no doubting the significance of the issue on mobile.