About to head off for your summer break? What may happen back home is always a concern; but if you want a bit more piece of mind, how about a live webcam view of what is going on in places you care about?
Of course you can easily purchase a security camera kit from your favourite electronic hobbyist store, but it is not a complete solution. Recording video to a hard drive is all very well, but what if the thief takes a hammer to it or even nabs it? Further, returning home to find two-week old footage of a break-in is of limited use compared to a live alert.
In other words, you need not only a camera but also a service. This used to be expensive, but does not need to be in the internet era. What about a cheap camera that sends images to a web site, enabling you to log in from anywhere and check what is going on? And how about an email or SMS alert triggered by motion detection?
This is exactly what Jabbakam does. The basic kit costs £59.95 and £5.95 per month, for which you get an IP camera and 14 days of video footage stored online. You can also use your own camera if you have a suitable one; the main requirement is that it supports motion detection, enabling the alerting feature, and reducing the number of images that need to be sent to the web service. More expensive subscriptions store video for longer; £13.95 per month gets you 90 days. SMS alerts cost extra.
Developed by a company based in Guernsey, the product is not so much the camera, but rather the web application and service. The camera itself is a simple but well-made affair, with a wall-mountable bracket and a swivel joint that lets you angle it. You can also adjust focus by twisting the lens.

Under the webcam are ports for wired Ethernet and power.

Given that the serial number starts YCAM I have a hunch it may be made for Jabbakam by Y-cam.
The camera must be wired to your broadband router. If you are on a business network you may have firewall issues; I tried on my own network and found it did not work behind the firewall, but have not investigated in detail.
So how about the service? I signed into Jabbakam and found that set-up was pretty much IJW (It Just Works). The camera was detected and I could view live images. Video is a slightly generous term, since each image is one second apart, and the quality is not fantastic, but gives you a good idea of what is happening. You can add additional cameras if you want fuller coverage of your home or workplace.
I also set up email alerting. This seems to work well. When the camera detects movement you get an email with a still image attached. Click the link in the email, and you can view the video. There is also an iPhone app that shows recent images. Advanced settings let you schedule alerts, for example to avoid having them active when you yourself are moving around.

Jabbakam is not just intended for security. The web service also has the concept of networks, which enable you to share your camera with others. The number is small at the moment, but I did see one called Birdboxes of Jabbakam which I guess is for ornithology enthusiasts.
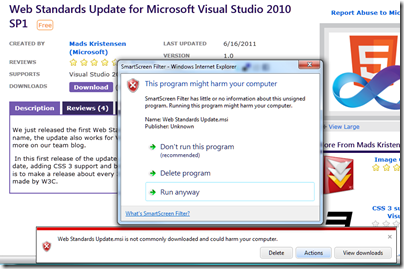
There was one aspect of Jabbakam that I found troubling. A mash-up with Google Maps lets you see where cameras of other users are installed, and clicking on a camera gives you the name and address of the user and a link to send a private message:

I discovered that this information sharing is on by default:

This surprised me, as I would have thought that a typical Jabbakam user would be sensitive about sharing these details.
Finally, I should mention that Jabbakam has a RESTful API for developers, though the documentation is incomplete at the moment and the application showcase is empty. Apparently this is being worked on, so watch the space if you are interested.
A good buy? On the plus side, Jabbakam seems to me nicely done, easy to set up, and delivers what is claimed: remote video monitoring of any indoor location. The alert service is particularly useful, though this only works if the camera is pointing somewhere that should normally be motion-free. For example, pointing the camera at a car parked on the street outside your home might seem a good idea, except that the alert would go off every time someone walked by. I should also observe that the supplied camera only works indoors, so it would need to be at a window.
There are questions of course about the effectiveness of CCTV security. Blurry pictures of hooded figures may not do you much good in terms of identifying the villains, though the alert service could be an advantage.
What are the social implications if large numbers of people choose to stick surveillance cameras all over their homes? I am not sure, but it is a question worth reflecting on.
That said, for someone on holiday who would like the ability to check that everything is in order at home, this seems to me a neat and smart solution.