Every major IT security incident generates a ton of me-too articles most of which lack meaningful content. Journalists receive a torrent of emails from companies or consultants hoping to be quoted, with insightful remarks like “companies should be more prepared” or “you should always keep your systems and security software patched and up to date.”
An interesting feature of NotPetya (which is also Not Ransomware, but rather a malware attack designed to destroy data and disrupt business) is that keeping your systems and security software patched and up to date in some cases did not help you. Note this comment from a user:
Updated Win10 CU with all new cumulative updates and Win10 Insider Fast latest were attacked and affected. Probably used “admin” shares but anyway – Defender from Enterprise just ignored virus shared through network.
Nevertheless, running a fully updated Windows 10 did mitigate the attack compared to running earlier versions, especially Windows 7.
Two posts about NotPetya which are worth reading are the technical analyses from Microsoft here and here. Reading these it is hard not to conclude that the attack was an example of state-sponsored cyberwarfare primarily targeting Ukraine. The main factors behind this conclusion are the lack of financial incentive (no serious effort to collect payment which in any case could not restore files). Note the following from Microsoft’s analysis:
The VictimID shown to the user is randomly generated using CryptGenRandom() and does not correspond to the MFT encryption, so the ID shown is of no value and is also independent from the per-drive file encryption ID written on README.TXT.
My observations are as follows.
1. You cannot rely on security software, nor on OS patching (though this is still critically important). Another example of this came in the course of reviewing the new SENSE consumer security appliance from F-Secure. As part of the test, I plucked out a recent email which asked me to download a virus (thinly disguised as an invoice) and tried to download it. I succeeded. It sailed past both Windows Defender and F-Secure. When I tested the viral file with VirusTotal only 4 of 58 anti-virus applications detected it.

The problem is that competent new malware has a window of opportunity of at least several hours when it is likely not to be picked up. If during this time it can infect a significant number of systems and then spread by other means (as happened with both WannaCry and NotPetya) the result can be severe.
2. Check your backups. This is the most effective protection against malware. Further, backup is complicated. What happens if corrupted or encrypted files are backed up several times before the problem is spotted? This means you need a backup that can go back in time to several different dates. If your backup is always online, what happens if a network intruder is able to manage and delete your backups? This means you should have offline backups, or at least avoid having a single set of credentials which, if stolen, give an attacker full access to all your backups. What happens if you think you are backed up, but in fact critical files are not being backed up? This is common and means you must do a test restore from time to time, pretending that all your production systems have disappeared.
3. If you are running Windows, run Windows 10. I am sorry to have to say this, in that I recognize that in some respects Windows 7 has a more coherent design and user interface. But you cannot afford to miss out on the security work Microsoft has done in Windows 10, as the second Microsoft article referenced above spells out.
4. Is it the fault of Microsoft Windows? An interesting discussion point which deserves more attention. The simplistic argument against Windows is that most malware attacks exploit bugs in Windows, therefore it is partly Microsoft’s fault for making the bugs, and partly your fault for running Windows. The more plausible argument is that Windows monoculture in business gives criminals an easy target, with a huge array of tools and expertise on how to hack it easily available.
The issue is in reality a complex one and we should credit Microsoft at least with huge efforts to make Windows more secure. Users, it must be noted, are in many cases resistant to these efforts, perceiving them as an unnecessary nuisance (for example User Access Control in Vista); and historically third-party software vendors have also often got in the way, such as being slow or reluctant to apply digital signatures to software drivers and applications.
Windows 8 was in part an effort to secure Windows by introducing a new and secure model for applications. There are many reasons why this was unsuccessful, but too little recognition of the security aspect of these efforts.
The answer then is also nuanced. If you run Windows you can so with reasonable security, especially if you are serious about it and use features such as Device Guard, which whitelists trusted applications. If you switch your business to Mac or Linux, you might well escape the next big attack, not so much because the OS is inherently more secure, but because you become part of a smaller and less attractive target.
For a better answer, see the next observation.
5. Most users should run a locked-down operating system. This seems rather obvious. Users who are not developers, who use the same half a dozen applications day to day, are better and more safely served by running a computer in which applications are properly isolated from the operating system and on which arbitrary executables from unknown sources are not allowed to execute. Examples are iOS, Android, Chrome OS and Windows 10 S. Windows 10 Creators Update lets you move a little way in this direction by setting it to allow apps from the Store only:
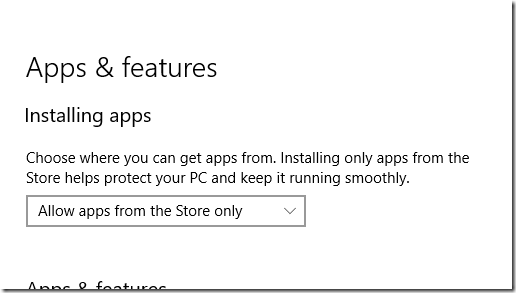
There is a significant downside to running a locked-down operating system, especially as a consumer, in that you cede control of what you can and cannot install to the operating system vendor, as well as paying a fee to that vendor for each paid-for installation. Android and iOS users live with this because it has always been that way, but in Windows the change of culture is difficult. Another issue is limitations in the Windows Store app platform, though this is becoming less of an issue thanks to the Desktop Bridge, which means almost any application can become a Store application. In gaming there is a problem with Steam which is an entire third-party Store system (apparently Steam bypasses the Windows 10 control panel restriction, though it does not run on Windows 10 S). Open source applications are another problem, since few are available in the Windows Store, though this could change.
If we really want Windows to become more secure, we should get behind Windows 10 S and demand better third-party support for the Windows Store.