A big story today concerns irregular activity on Apple’s iTunes store, the one and only means of purchasing applications for iPhone and iPad and central to the company’s strategy. The reports allege that developers are hacking iTunes accounts to purchase and give favourable review to their apps – which can only be a short term strategy since you would imagine that such activity would soon be detected and the perpetrators traced through the payment system.
As it happens I’d been meaning to post about iTunes security in any case. I blogged about an incident just over a month ago, since when there have been a steady stream of comments from other users who say that their iTunes accounts were hacked and fraudulent purchases made.
A recent comment refers to this thread, started over a year ago and now with over 200 comments from similarly afflicted users.
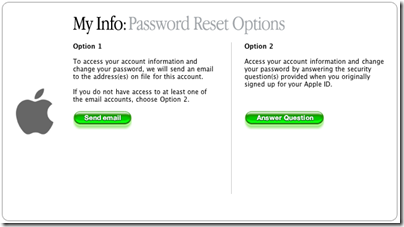
Despite the number of reported incidents, there is no reason to suppose that Apple’s servers have been broken into. Several other mechanisms are more likely, including malware-infected computers on which users may have stored passwords, or have keystrokes logged; or successful attempts to guess passwords or the answer to so-called “security questions” which also give access to account details.
Such questions should be called insecurity questions, since they are really designed to reduce the burden on helpdesks from users who have lost passwords or access to obsolete email accounts. Since they allow access to accounts without knowing the password, they reduce security, and even more so when the questions are for semi-public information like mother’s maiden name, which is commonly used.
Given the number of iTunes accounts, it is not surprising that there are numerous successful hacks, whether or not there is some issue (other than the insecurity questions) with iTunes or Apple’s servers.
That said, there is a consistent theme running through all these threads, which is that Apple’s customer service towards victims of hacking seems poor. Contact is email-only, users are simply referred to their banks, Apple promises further contact within 24 hours that is often not forthcoming, and there are reports of users losing access to credit or previous purchases. It was an instance of the latter which prompted my earlier post.
Apple therefore should fix its customer service, even if its servers are watertight. I’d like to see it lose the insecurity questions too.